All right, all you wannabe hackers. All you up-and-coming security freaks and as-yet untested marauders of the airwaves. If you don’t know much about wireless security but still need to look the part for your clique, wifite has a solution for you.
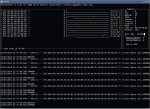
By the author’s own admission, wifite is intended to streamline penetration attempts on wireless signals. I’ve done enough with simple signal cracking to know that, at its best, unlocking a network can be a little time-consuming, and require a small measure of expertise.
At its worst, I can only imagine the time and effort it would take. 😐
So if you’re mostly uninformed and need a means of getting revenge on your next door neighbor, or if you’re already an expert and just don’t want the hassle of juggling three or four programs, or if you foolishly relinquished your password to the Windows wireless access tool and now you can’t remember what it was … wifite has all the shortcuts for you.
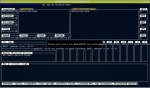
Just about everything with wifite is to my liking. Plenty of information up front, buckets and buckets of color, a menu-driven system and feedback galore. It’s relatively light and relatively easy to work. If you can pick a number off a list, wifite can do the rest.
But success in wireless security, in spite of what Hollywood might tell you, isn’t just a matter of pushing buttons and getting a password. If you don’t know or understand what wifite is doing, then, as the author suggests, you should probably do a little homework first.
So don’t take wifite as some sort of springboard to the elite ranks of wireless crackers. You won’t win any points among the knowledgeable geeks by stealing your ex-girlfriend’s wireless password if you let it be known you used wifite in your criminal escapade.
Find out why it works, how it works and when it works, and then wifite will make more sense when you put it to work.